Security measures for the Internet of Things (IoT) which is proliferating across the globe.
NTT Com Global Watch vol.5
2015/4
At the end of 2014, the Japanese government began an overhaul of its information technology policy in order to improve the global competitiveness of Japanese industry. The government is facilitating discussions by the Information Economy Subcommittee of the session meeting for the Commercial Affairs Information Distribution within the Industrial Structure Council. The talks concern standardization and systematization in order to promote the utilization of big data by all industries including the manufacturing industry. Its aim is to promote the utilization of strategic ICT and reform industry in Japan with global practices, starting from inside Japan. In other words, it is a modern industrial revolution. The context for this is the promise of big data on a global scale due to the development of the "IoT" (Internet of Things).
The Internet of Things continues to expand
Nowadays it is not just information terminals such as PCs and cell phones that are networked. Recently networked devices have expanded to include monitoring cameras, vending machines, industrial machinery, motor vehicles and a variety of meters and sensors. By 2020, their number is predicted to grow to from 30 to 50 billion. Furthermore, some say that this will develop into the "Trillion Sensors Universe," a society in which one trillion sensors are used annually.
IDC Japan, a survey firm specializing in IT, predicted in their world IoT market forecast that was announced in November 2014 that the market scale will grow from 1.3 trillion dollars in 2013 to 3.04 trillion dollars in 2020. The forecast points out that "In the short term North America will drive the market, but by 2020 the number of IoT devices in Western Europe and the Asia Pacific region will exceed that of North America, due to a boost from government markets and their emphasis on a more open environment."
It says that IoT will proliferate in Japan in the same way it does throughout the world, and that the market will continue to grow. According to a forecast by IDC Japan announced in February 2015, the domestic IoT sales volume is set to increase from 9.4 trillion yen in 2014 to 16.4 trillion yen in 2019. The number of IoT devices is also predicted to increase, from 557 million in 2014 to 956 million in 2019.
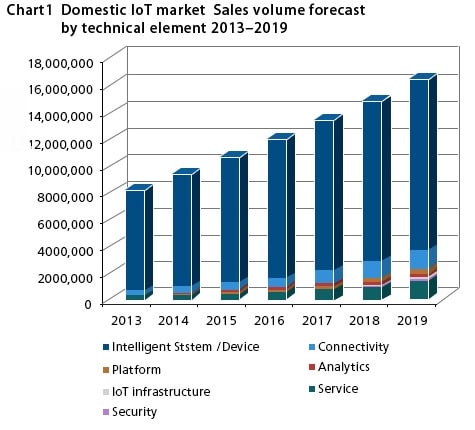
※Actual values are shown for 2013, forecast values are shown for 2014 and predicted values are shown for 2015-2019
Source: IDC Japan (February 2015)
Back to top
Increased risks with the proliferation of IoT
With the development of IoT, everything will be connected to the network, either directly or via a meter or sensor, and big data will be generated through the collection and accumulation of miscellaneous data. Analyzing and using this data in line with goals and applications will enable the creation of new innovations. For example, increased safety of public infrastructure, greater energy efficiency, increased industrial competitiveness, improved quality of products and services, and richer, more convenient day to day lives.
On the other hand, we cannot forget the increased risk that accompanies IoT proliferation. When all things are connected to the network, they are also subject to cyber attacks. In particular, a cyber attack that stops the normal operations of critical infrastructure systems that monitor and control equipment and machinery that supports society, industry and the economy will lead to serious accidents and serious damage. Incidentally, the National Center of Incident Readiness and Strategy for Cybersecurity (NISC) has defined 13 areas of critical infrastructure.
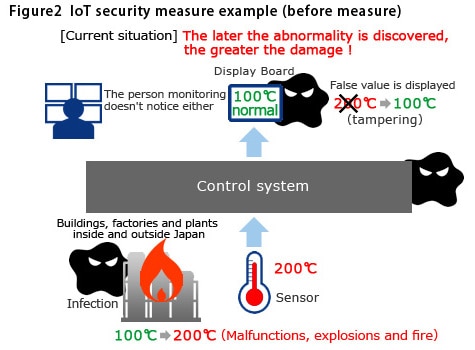
Akira Sakaino, an expert in IoT and Senior Manager of NTT Communication's Technology Development Division explains the following about the risks that come with IoT proliferation. "Let's say that the control system at a chemical plant is subject to a targeted threat. Under normal circumstances, the values for temperature and pressure etc. that are sent from the sensors in each machine are collected by the control system, which monitors the machine's running status and controls it safely. The operating information data, which consists of values etc. monitored by the control system is displayed on the display panel in the control room, and a person responsible for monitoring is constantly checking it. However, there is a risk of someone introducing a virus into the system that tampers with control room data display panel. So, even if an abnormality occurs in the equipment, it will continue to display normal values. If this happens, the person monitoring will not realize, even if the equipment is excessively hot and at high pressure, and the machine could explode and burst into flames." (Sakaino)
Back to top
Ensuring security is a precondition for using IoT
Takashi Horikoshi, responsible for IoT areas of the Technical Development Division at NTT Com, says, "In reality, any number of explosions and fires occur in domestic chemical plants. At chemical plants, raw materials are produced for a variety of products, and fuels are produced for use in a variety of industries. If the supply decreases, the economic impact will also increase. However, the fact is that many times the cause of large accidents at chemical plants cannot be identified. This is because the devices that recorded the operating data end up being destroyed in the fire. If the cause cannot be identified, it is not possible to work out a solution. In these cases, operations continue but the risks remain."
Therefore we cannot rule out the possibility that some of the accidents at chemical plans that have occurred up to now were caused by cyber attacks on control systems.
Shin Miyakawa, who holds a Ph.D. in Engineering and is the general manager responsible for the Engineering Development Division, is the Network Evangelist at NTT Com. Miyakawa comments, "Equipment and devices that support critical infrastructure like chemical plants are connected to control systems in a closed network. However, being closed does mean that it is safe. No matter what network, security measures are always needed. When you have precise security measures matched to network type and use environment, you can utilize IoT over a wider range of areas."
As one example of security measures for the chemical plant used as the example, Miyakawa proposes "behavior monitoring" using VPN and a secure private cloud. It is a set up where the machine operating data is sent to the control room via a different route than that used for the equipment and control system, and the network that connects the control room display panel.
Even in the unlikely event of a cyber attack on the control system that tampers with the operating data, safety can be maintained because the correct operating data is sent in real time, and the system on the private cloud detects the abnormal signs.
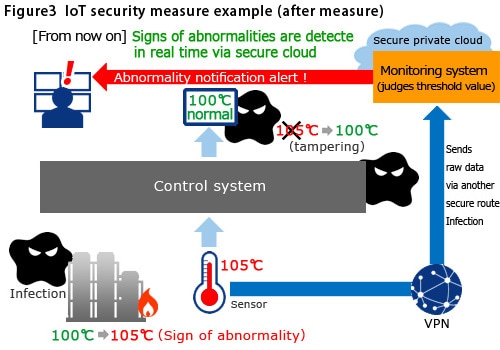
Miyakawa says, "Here is a hypothetical example. If someone picked up a USB memory stick that had fallen in the factory parking lot and inserted it into a terminal connected to the system in the facility, it could spread a virus via the network that was supposed to be closed. If you don't hypothesize every possibility when you put together security measures, you cannot maintain safety. The first step in IoT proliferation is to make efforts with network security measures, and it is a critical issue," he emphasizes.
Back to top
NTT Com's IoT know-how is built up through validation experiments
Up to now NTT Com has continued to provide networks and services that can support corporate and organizational lifelines for many businesses in the critical infrastructure field, whose work and services absolutely cannot stop. In addition NTT Com is amassing experience and know-how for the establishment of security measures in the IoT area by building up a large number of initiatives, in order to support the imminent proliferation of IoT.
For example, we are collaborating with the virtual group Virtual Engineering Community (VEC), which is engaged in activities for the proliferation of control system security aimed at areas such as manufacturing industries, buildings, energy and electric power. We are engaged in validation experiments for "Industry4.1J", which is leveraging secure global information communication infrastructure to improve the productivity of factories, plants and buildings, and to increase the efficiency of maintenance operations.
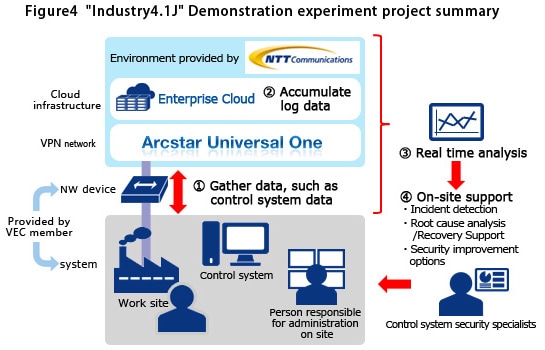
The purpose of this validation experiment project is to confirm the technical requirements of the communication infrastructure that is instrumental in ensuring safety and efficiency on the production floor. For example, the ability of the current network and cloud infrastructures to support the frequency, speed and volume of data communication occurring between the production floor and the cloud, and which are necessary for remote monitoring of the control system.
For this project NTT Com is providing "Enterprise Cloud," a secure cloud environment, and "Arcstar Universal One," a secure VPN network, in order to develop a secure ICT environment which is essential to the remote monitoring of critical infrastructure.
As the IoT field proliferates globally, NTT Com will continue to provide secure network and cloud environments which protect the safety and security of infrastructure that supports lifestyles and industries across all countries and regions.

Dr. Shin Miyakawa
Network Evangelist
Director
Technology Development
Akira Sakaino
Senior Manager
Technology Development
Takashi Horikoshi
Technology Development
 EN
EN

